Let me tell a little story ‘bout an email phish,
I foiled the attempt, but not the way I might have wished…
The line is cast
While I was checking out my business account email a few days ago I happened upon a really strange message. Here in my Inbox sat an email from Google, of all places, a message I was pretty sure had no business being there. A sly smile came to my face and I opened it to see what it had to say to me. Have a look:
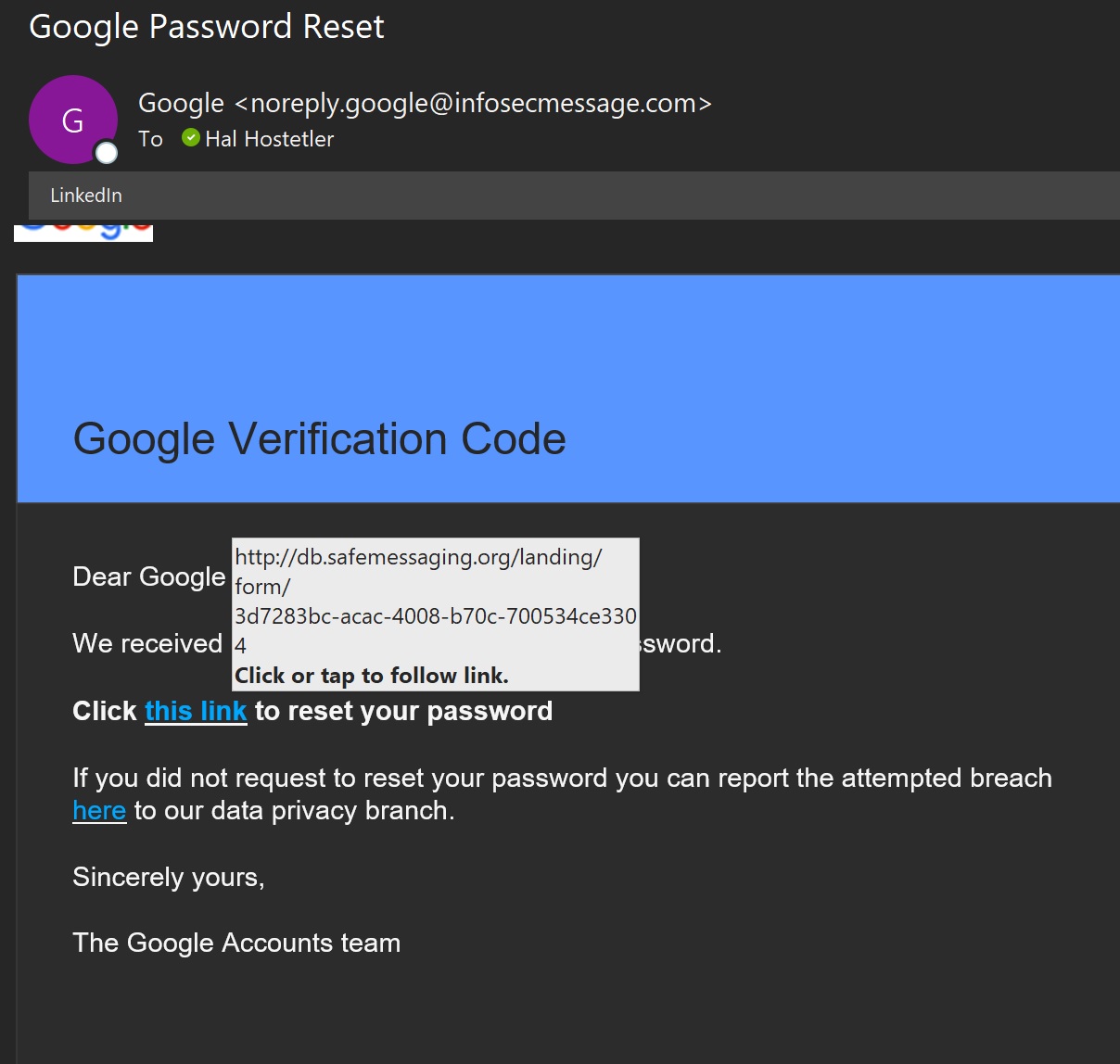
Yup. This email flat REEKS of a phishing attempt. First of all, it’s not from Google, rather, some outfit called infosecmessage.com. Second, it miserably fails the URL test, the actual destination address of the this link and here links is safemessaging.org and the word Google is nowhere to be found.
The Bait is Intentionally Taken!
What to do with an obvious phishing attempt? I guess I was in a testy mood, I decided to have a little fun with it. In my last article, I talked about the Windows Sandbox app and its virtues, I decided this phishing attempt would make a good test case for it. So, I fired the Sandbox up, copied the URL from the email, started Edge, entered the URL and waited. The expected login screen came up, I filled it out with fake, fairly unfriendly, data, and hit “Enter”. My next task was to report then site as a fake using the Edge “Report Unsafe Site” feature. So much for that, I closed the Sandbox and went on about my business.
The Unexpected Oops!
I thought I was through with this site, imagine my surprise when this email appeared in my Inbox:
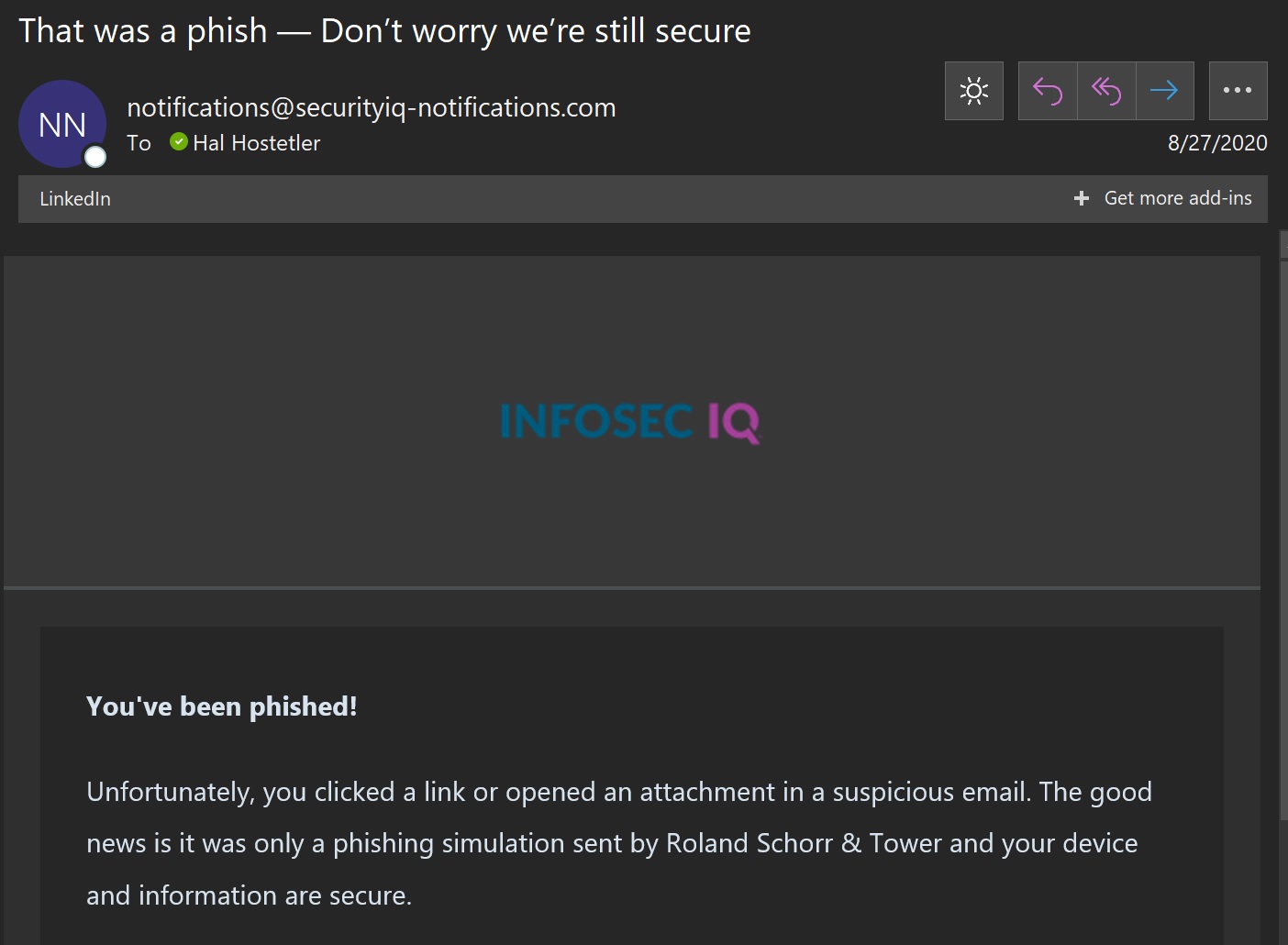
Wow! Despite the precautions I’d taken, I got myself gigged! So, while those precautions kept me, my device, and the business network safe, they didn’t protect me from being caught in a phishing sting the company, itself, promoted. My first concern was what happened on the back end of this, some of the things I had to say on the phishing screen were not at all friendly to whoever the author(s) might be. Thankfully, that part was not tracked!
The Take-aways
I must admit I was not expecting this. That, by the way, is the whole idea behind running a compliance test, it is not expected and is designed to see how the recipient will respond to it. The link, itself, had an identification factor that showed me as the recipient, and I’d have been gigged regardless of how I went about getting there. Since I failed this test, here are some suggestions:
- Learn how to recognize phishing emails.
- If you get one, don’t just assume its from someone out on the net, you might be being tested, like I was.
- Don’t click the link, even to report it as an obvious phishing attempt.
- Report the email to your security folks.
Microsoft has a good article on protecting yourself from phishing, please look it over: